-
Solutions
Back
Digital Trust for:
Enterprise IT, PKI & Identity
Code & Software
Documents & Signing
IoT & Connected Devices
Manage PKI and Certificate risk in one place
Manage PKI and Certificate risk in one place
The smarter way to manage certificate lifecycles
Continuous Signing for CI/CD & DevOps
Secure, flexible and global signing
Trusted from silicon to in-the-field
Device security without compromise
Accelerate secure app development
Streamlined Certificate
Management
and Automation:
Delivering At-Scale Uptime
and Availability
2022 Edition of the TLS/SSL Best Practices Guide

2022 Edition of the TLS/SSL Best Practices Guide


How to establish a signing policy DevOps will actually adopt

Global perspective on managing document signing and regulations

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale
DOWNLOAD NOW -
Buy
BackWildcard DomainBUY
Find the right TLS/SSL Certificate to secure your website
eIDAS-compliant transaction and website document security solutions
-
Insights
Back
Digital Trust for the Real World
Explore these pages to discover how DigiCert is helping organizations establish, manage and extend digital trust to solve real-world problems.
Ponemon Institute Report
See what our global post-quantum study uncovered about where the world stands in the race to prepare for quantum computing.
LEARN MORE >
-
Partners
Back
-
Support
Back
CONTACT OUR SUPPORT TEAM
- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
- Contact us
- Language
DigiCert® IoT Trust Manager
IoT device management with end-to-end security
Centrally manage IoT connected device identity,
authentication and encryption from silicon to field.
That's digital trust for the real world.
The complex IoT
device landscape
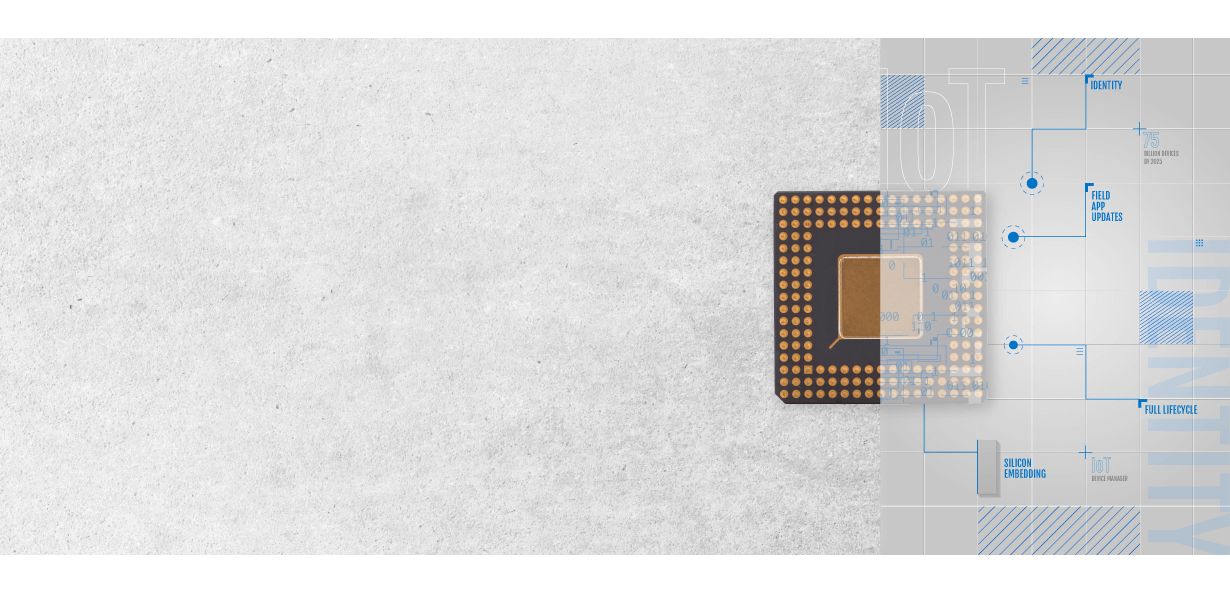
Every day, people are inventing new ways to connect IoT devices. The most recent estimates predict as many as 75 billion will be online by 2025. Securing so many devices—each with its unique manufacturing process, electronics, software, function and lifecycle—requires a uniquely flexible, scalable and trusted solution for IoT device management.

Billions of IoT devices. One solution.
DigiCert® IoT Trust Manager uses modern PKI to deliver digital trust that meets the needs of even the most demanding IoT device deployments. From silicon injection to sunsetting, manufacturing floor to the field, or single remediation to the nearly simultaneous issuance of millions of certificates, DigiCert IoT Trust Manager is the simple and scalable IoT security platform for device identity, integrity, and control.
Total IoT device awareness
Manage discovery, reporting, certificate creation and revocation, user access and permissions, all in one place.
Adaptable integration
Make your security work easily with any number of systems, using REST API, SCEP, EST and CMPv2.
Efficient management
Save time and prevent lapses with automated backups and updates on fast, high volume-issuing container-based architecture.
Quicker deployment
Securely roll out new services throughout your production in minutes with near-instant ICA creation and advanced permissions.
A comprehensive IoT security platform
Our end-to-end IoT device security solution delivers development simplification, time-to-market acceleration, security improvements, and full ecosystem enablement. Whether you are a chip manufacturer, a device maker, or a device operator, DigiCert IoT Trust Manager provides trust for all IoT device security needs at all stages in the lifecycle.
IoT device trust
- Trusted identity
- Key protection/generation
- Device certificate issuance
IoT device provisioning
- Signing code/firmware
- Secure firmware updates
- Secure device configuration
IoT device operations
- In-field device monitoring
- Certificate and key management
- Signature/certificate validation
- Manual authentication
- Secure communications
- Secure device boot
- Device enrollment to cloud services

Healthcare IoT
Protect patient data while securing smart care devices like pacemakers and continuous glucose monitors.

Home and Consumer IoT
Secure home networks and protect private data for everything from routers to cameras to wearables.

Industrial IoT
Build secure identity into the manufacturing process, with options from silicon injection to assembly and beyond.
Smart Cities IoT
Maximize smart grid efficiency and protect the real-time data shared between meters, sensors and systems.

Transportation IoT
Encrypt and identify sensors and systems that monitor and control all types of vehicles—sea, land, air and space.
- 1
- 2
- 3
- 4
- 5
Simplicity at scale
Deploy anywhere
Choose from DigiCert-hosted, in-country, on-premises, in your cloud or anywhere between
Scale for anything
Meet your evolving needs with a flexible, highly scalable container-based infrastructure
Control everything
Embed all devices with proactive management for identity, integrity and authentication
End-to-end security and operations with DigiCert + Mocana
Control devices in the field with the industry standard in end-to-end device trust and operations management.
Embed and manage:
- Unalterable identifiers for secure identity
- Device-hardening applications
- Rules-based network access control
- Greenfield and brownfield interoperability
- OTA, air-gapped, and OTW provisioning and updates
- Granular monitoring, analysis, and mitigation
- OS templates for acceleration on any system
- Lightweight cryptography that supports limited storage
- Pre-built APIs and your choice of coding language
Matter compliance with trusted IoT management
As a device manufacturer or maker, you can meet Matter compliance for interoperablity with DigiCert IoT Trust Manager.
- Issue Device Attestation Certificates (DAC) into any size and type of manufacturing process
- Easily meet compliance thanks to seamless integration with existing operations
- Maintain compliance with OTA field updates that can push out to any number of devices

Adaptive. Aware. Attributed. All in ONE.
For two decades, DigiCert has been at the forefront of the PKI evolution, driving the world’s most trusted security solution into new territories and new eras of technological innovation. New deployments, new configurations, new applications, new toys and new tools—no matter what we invent, PKI evolves to protect.
Now, DigiCert is ushering PKI into its next stage of evolution with DigiCert ONE. Built with a modern, holistic approach to PKI management, DigiCert ONE allows you to rapidly deploy in any environment, roll out services in a fraction of the time, and deliver end-to-end user and device management at any scale.
A foundation for digital trust
DigiCert ONE is more than just a platform. It’s a new way of thinking about how you secure and manage everything of value in your organization. From the individual website to the massive enterprise, DigiCert ONE makes security, validation, and identity powerful and easy. No matter the size or use, DigiCert ONE delivers control and simplicity for the highest level of assurance.
Take a look at our other DigiCert ONE managers
DIGICERT® CERTCENTRAL TLS MANAGER
DIGICERT® TRUST LIFECYCLE MANAGER
DIGICERT® SOFTWARE TRUST MANAGER
DIGICERT® DOCUMENT TRUST MANAGER
Already using DigiCert ONE? Log in now.
DigiCert IoT Trust Manager RESOURCES
TALK TO AN EXPERT TO LEARN HOW DIGICERT SOLUTIONS
CAN HELP YOU DELIVER DIGITAL TRUST
-
Company
-
My Account
-
Resources
-
Solutions
-
© 2024 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings