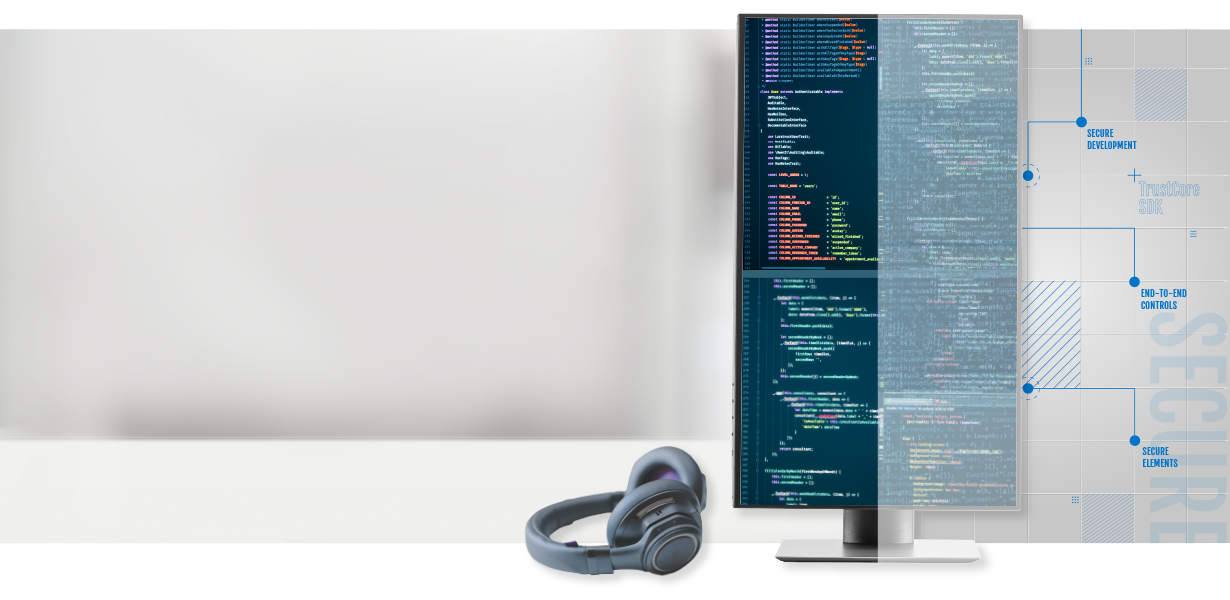
DigiCert® TRUSTCORE SDK
The security toolkit built for developers
Empower your IoT-embedded development and accelerate your product’s time-to-market with a toolkit of expert-backed, security-focused libraries.

The difference between developing for each device and developing for every device
Empower your smart innovations with secure IoT application development—at a global scale, no constant reengineering required.
Deploy to various hardware platforms and operating systems without the need to rewrite for smooth, universal integration across any OS or programming language.
A footprint for any form factor
From high-powered processing to lightweight encryption, DigiCert TrustCore SDK’s flexible architecture supports a broad spectrum of devices with different memory requirements.
Use your preferred language
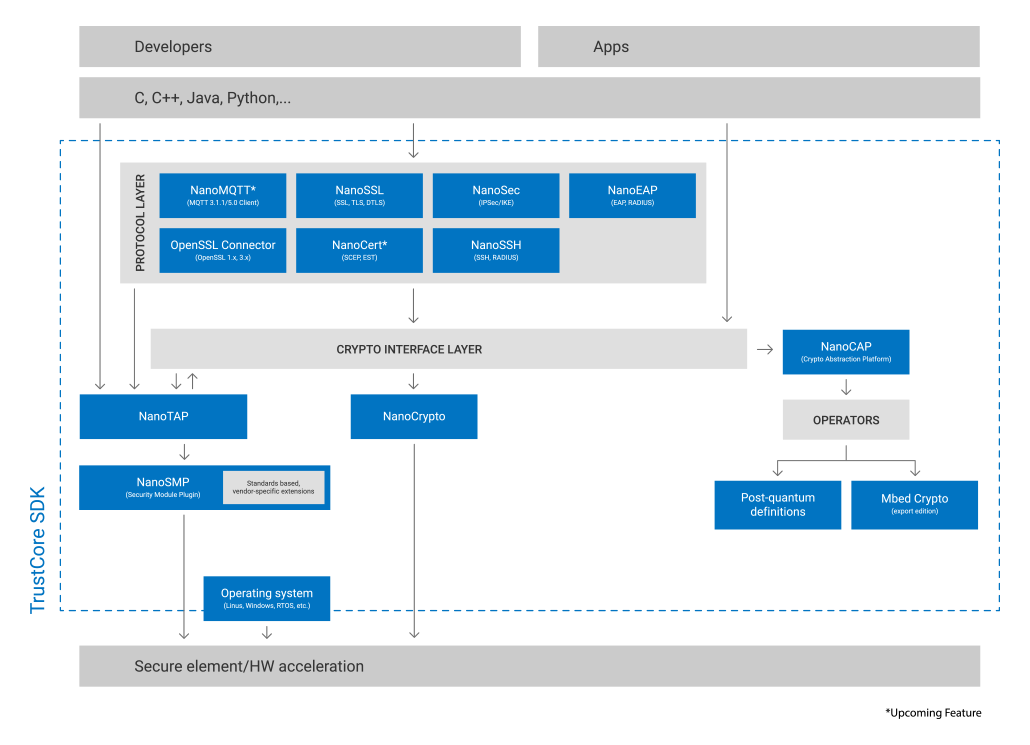
TrustCore SDK integrates with your existing codebase, offering compatibility with a wide array of APIs and programming languages, such as C, C++, C#, Java, and Python, to maintain your development workflow without the need for translation or rewrites.
Implement end-to-end controls—without endlessly rewriting code
A simple set of APIs makes it possible to integrate with any Secure Element, ensure data privacy and protection, and comply with import/export controls without extensive reengineering for each application.
DigiCert TrustCore SDK in action
Transform application development from cost center to revenue center
Drastically cut lifecycle maintenance costs and enhance profitability with our efficient, security-first approach, paving the way for cost-effective innovation and limitless potential for new revenue.
TRUSTCORE SDK
Developer Documentation
WEBINAR
Protecting the IoT Device Lifecycle

WHITEPAPER
Powering Progress in EV Charging









